Network security, everywhere, but especially in Data Centers is of the utmost importance. Knowledge, of what is going on inside your private network is invaluable. Until recently, network security was completely preoccupied with protecting network only from the outside sources. Because of fast development and introduction of new technologies, pool of potentially vulnerable applications and protocols is quickly increasing. The confidence, we felt years ago, that applications alone will properly handle and repel ever increasing number of attacks, which become more and more sophisticated is thoughtfully shaken if not outright wrong. Security breaches will happen (not if), but without knowledge of what is going on in our networks we are powerless to act. With compromised or badly written applications, edge Firewalls alone can’t provide needed network protection.
One of the solutions for these problems are Intrusion Detection and Prevention systems (IDS/IPS). Properly configured Intrusion Detection System (IDS) can detect anomalies in internal networks, for incoming (before the fact) and outgoing traffic (after the fact). In Intrusion Prevention mode (IPS), anomalies are not only reported, but also actively blocked.
M2DC security appliance utilizes open source project Suricata for its next-gen firewall solution. Suricata utilizes parallel processing of network traffic, providing significant performance increase compared to a single threaded IDS applications. With multi threaded approach, Suricata can achieve significantly higher throughput and is capable of real time 10 Gbit and faster network traffic inspection. Currently, Suricata can achieve this only by utilizing powerful x86 CPUs like Xeon family.
Older version of Suricata could employ CUDA for even faster traffic analysis. In its current version 3.2.2 CUDA support is broken and unsupported. Utilizing older version doesn’t make any sense, since new version employs number of performance and functionality upgrades. Performance wise, Suricata version 3 employs completely parallel traffic inspection from traffic capture to output.
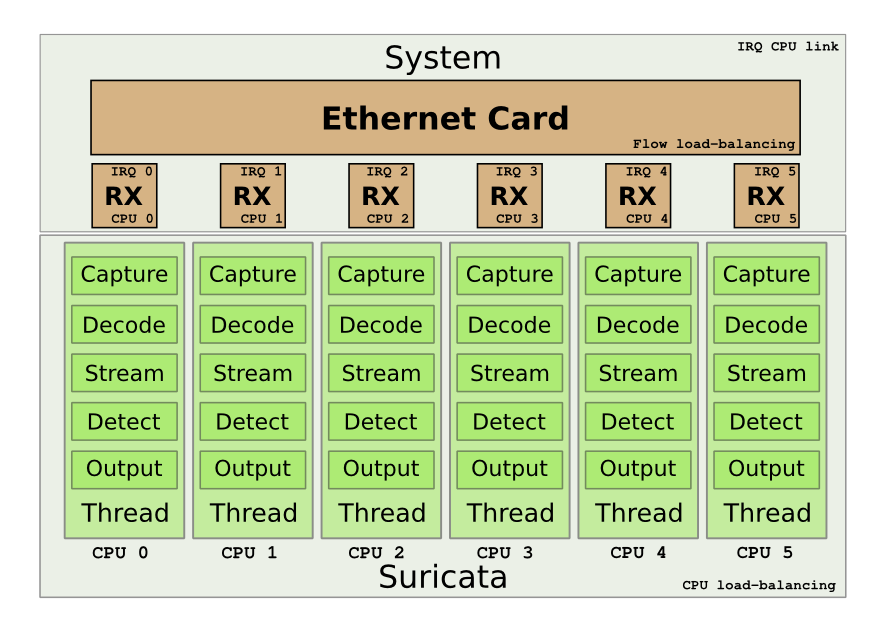
Illustration 1: Suricata parallel traffic inspection.
© All rights reserved by authors Peter Manev, Matt Jonkmann, Anoop Saldanha and Eric Leblond,
“Suricata, to 10Gbps and beyond,” 2012.
https://home.regit.org/2012/07/suricata-to-10gbps-and-beyond/
But not all traffic can be analyzed inside a single thread. For HTTP, tunnels and other encoded traffic Suricata spawns new threads. Here a possible performance improvement can be achieved by utilizing modern OpenCL approach, but this would require significant effort.
Security appliance inspects traffic with daily updated threat rule set. In case harmful traffic that trips DROP rule is detected, Suricata blocks offending network stream and logs alarm. Harmless traffic is left alone, all interesting events, which are configurable, are logged. Besides logged alarms, Suricata also logs arbitrary amount of network traffic. Logging is defined at start in configuration file, and can be used for more detailed analysis with specialized security software like Wireshark (https://www.wireshark.org).
Suricata can log vast amounts of interesting information, Netflow and Flow data, HTTP traffic, SMTP, IMAP, POP3, TLS, … or just alerts, that are tripped by threat rules. Logging additional data requires large amount of storage space. A corporate computer network with more than 300 connected networking devices produces more than 25 GB of data per day, so available storage is a serious consideration.
Encrypted traffic, for instance SSL and SSH can’t be analyzed. We are investigating possible solution for analysis of SSL encrypted HTTP traffic by use of open source Web Proxy product Squid (http://www.squid-cache.org). Squid could possibly serve as a SSL termination point. After SSL termination, traffic would be routed through Suricata, but this is still untested scenario and needs further analysis.
Since Suricata outputs all its findings in log files, we also need a more human friendly user interface. Currently we are testing a very interesting web based open source product especially written for Suricata, Evebox (https://evebox.org). Evebox is a very interesting product since it can be used in a very lightweight configuration, with a very lightweight embedded SqLight database back end.
With a deploy of Elasticsearch database back end, Evebox can provide detailed reports, besides the security event alerts, but at the considerable cost of memory and storage space.
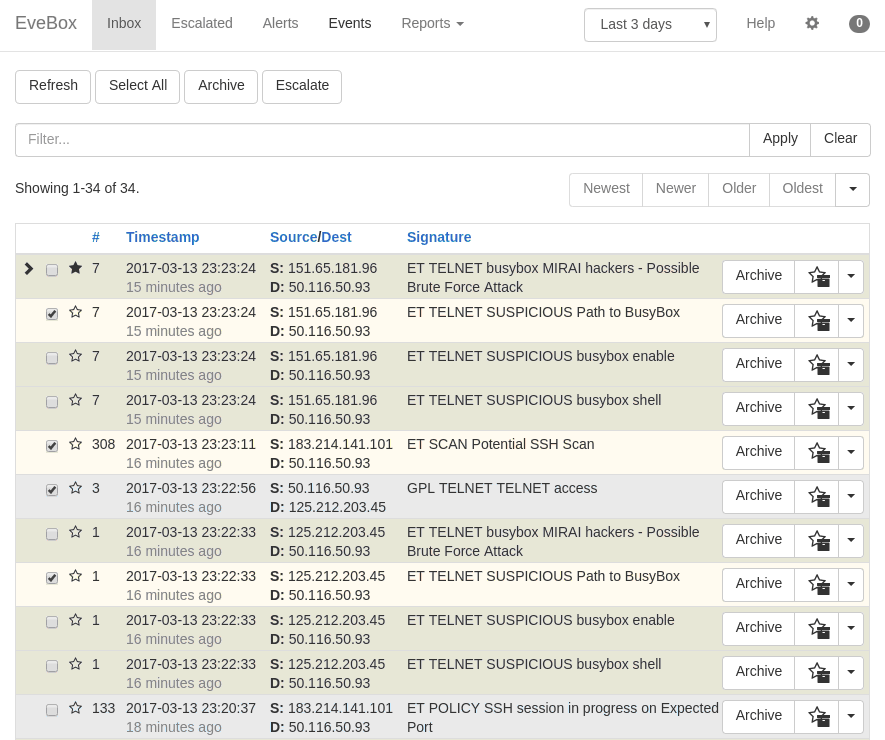
Illustration 2: Evebox main screen.
Porting of the Suricata on M2DC cost-optimized server architecture enables seamless integration of IDS/IPS solution with the microservers, providing next generation IDS/IPS for datacenters.








