This post was originally published on the
XLAB Steampunk blog.
Is there anything worse than working with unreliable Ansible Playbooks, exposing yourself to security risks and broken automation?
Well, we could name a few things but this is definitely at the top of the list.
Most of the time, you put your playbooks at risk without even realizing it because they depreciate in quality and reliability with every Ansible upgrade. Updating them can be a daunting task — investing hours into analyzing and upgrading your Ansible content. But, luckily for you, it doesn’t need to be.
There’s a variety of tools to help you write Ansible Playbooks, scan them for improvements and support your journey toward reliable automation. In this blog post, we’ll summarize the 5 most popular ways to scan and update your playbooks:
- Steampunk Spotter
- Ansible Lint
- KICS
- Ansible Later
- Molecule
But, before we dive deeper into these tools…
What are the different types of Infrastructure as Code (IaC) scanners?
IaC scanning tools come in all shapes and sizes. Some only focus on one type of IaC, such as AWS CloudFormation or Hashicorp Terraform, while others can scan multiple IaC types.
The latter is clearly more versatile and can save you the trouble of dealing with multiple tools. But, in general, IaC scanners can be split into the following categories:
- SAST (Static Application Security Testing) tools can scan source code at their design phase before the deployment (usually referred to as linters);
- DAST (Dynamic Application Security Testing) tools are used to analyze the code (and its responsiveness) that is already running;
- SCA (Software Composition Analysis) tools specialize in analyzing all IaC dependencies;
- IAST (Interactive Application Security Testing) tools combine SAST and DAST;
- ASTaaS (Application Security Testing as a Service) tools are services that perform testing for clients (e.g., enterprises).
Now that we understand the general IaC scanner categories, let’s see how the 5 aforementioned tools support your Ansible Playbook writing and updating journey.
1. Steampunk Spotter
Steampunk Spotter provides an Assisted Automation Writing tool that analyzes and offers recommendations for your Ansible Playbooks.
The tool uses a unique approach that enables users to automatically update their playbooks with little to no effort. You can either use the web interface or use CLI.
Steampunk Spotter goes beyond the simple syntax checks. By understanding the context of Ansible Playbooks and Collections, Spotter knows what you want to achieve with your playbook and helps you get there faster.
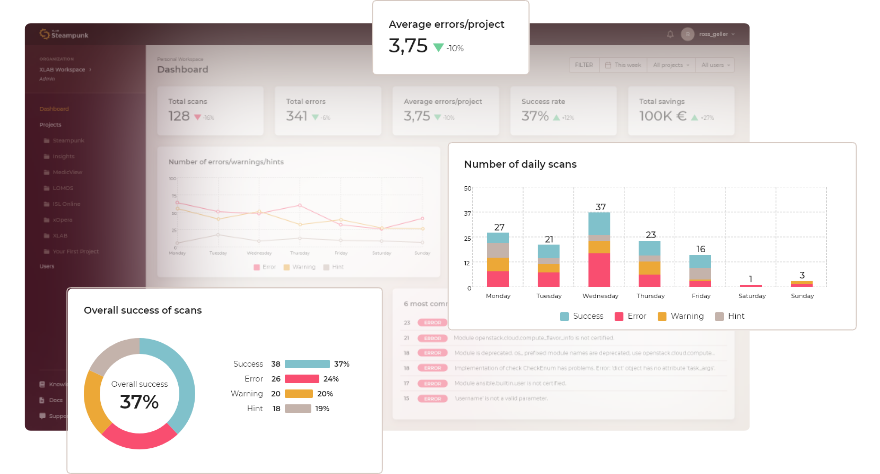
Spotter helps you check:
Best practices: Structure your playbooks for readability, collaboration and ease of use, and avoid common playbook anti-patterns.
Errors: Rely on the assistant that will guide you through hidden obstacles causing hard-to-catch and time-consuming errors.
Modules: Identify name changes and redirects, check for fully-qualified names and ensure you’re using certified and approved modules.
Parameters: Make sure you’re using correct parameters, considering their relationships and quickly identifying invalid configurations.
Upgrade paths: Run your playbooks when a new Ansible version is released and get recommendations with automated suggestions on how to make them compatible with the new version.
Spotter also integrates with GitHub and GitLab, enabling the scanning of Ansible content within the GitHub and GitLab CI/CD workflows, and supports VS Code integration.
“The Spotter seems like a very good addition to existing tools like ansible-lint and ansible-test. Especially the tips and hints to migrate from older Ansible versions to current versions as well as the function to fix found errors are great!’’ — Sebastian, System Engineer
2. Ansible Lint
Ansible Lint is another tool to check your Ansible Playbooks, roles and collections for practices and behavior that could potentially be improved.
The platform doesn’t offer a dedicated app. Instead, it brings a command-line tool (CLI) for linting Ansible Playbooks, roles and collections.
To evaluate Ansible content, Lint uses a set of rules. Users can define custom rules (and then use them along with default rules) by extending AnsibleLintRule Python class.
Here are some of the default rules:
- Indicate the use of features that are removed from Ansible
- By default, newly introduced rules trigger only warnings
- Possible indications that consequent runs would produce different results
- Anti-pattern detected, likely to cause undesired behavior
- Invalid metadata, likely related to galaxy, collections or roles
- Rules related to potential security issues, like exposing credentials
- Warnings about code that might not work in a predictable way
- Fatal errors indications that cannot be ignored or disabled
When scanning, CLI suggests having a collection structure. When no arguments are passed, the tool will use its internal heuristics to determine file types (i. e., to find Ansible Playbooks, roles and collections).
Users can add multiple Ansible Playbooks for scanning.
3. KICS
Keeping Infrastructure as Code Secure (KICS) is an open-source solution for static code analysis of Infrastructure as Code. The tool was created by Checkmarx, a global leader in application security testing.
KICS finds security vulnerabilities, compliance issues and infrastructure misconfigurations in the following Infrastructure as Code solutions: Terraform, Kubernetes, Docker, AWS CloudFormation, Ansible, Helm, Google Deployment Manager, AWS SAM, Microsoft ARM and OpenAPI 3.0 specifications.
The solution includes over 2000 fully customizable and adjustable heuristics rules, called queries, that users can edit or extend. Queries cover a wide range of vulnerability checks for AWS, GCP, Azure and other cloud providers.
4. ansible-later
ansible-later helps make Ansible roles more readable for all maintainers and can reduce troubleshooting time. It is a best practice scanner and linting tool and it helps to have a coding or best practice guideline in place. It also makes Ansible roles more readable. The tool is fast and easy to use. However, Ansible recommends that users use Ansible Lint for a more in-depth analysis.
ansible-later comes with a set of built-in checks, which focus more on Ansible syntax and doesn’t cover in-depth analysis.
5. Ansible Molecule
Ansible Molecule was designed to aid in the development and testing of Ansible roles. Molecule will simply run the converge action twice and check against Ansible’s standard output. It provides support for testing with multiple instances, operating systems and distributions, virtualization providers, test frameworks and testing scenarios.
Which one should you choose?
Honestly, there’s no one-size-fits-all approach to these scanners. They all complement each other in different ways, ensuring that you get the best possible results.
But, if you have to start somewhere, choose a tool that can help you not only scan your playbook but also automatically update errors. Start your free trial today.








